On Friday May 1st 2020, Quebec received a shipment of medical equipment destined to the people fighting COVID-19. An Antonov 225 was carrying the goods. The flight was organized thanks to a joint collaboration between Nolinor, Momentum Solutions and Antonov Airlines.
Departing from Tianjin, China, the plane made a stopover in Anchorage, Alaska, before continuing its flight over Canada towards the province of Quebec.
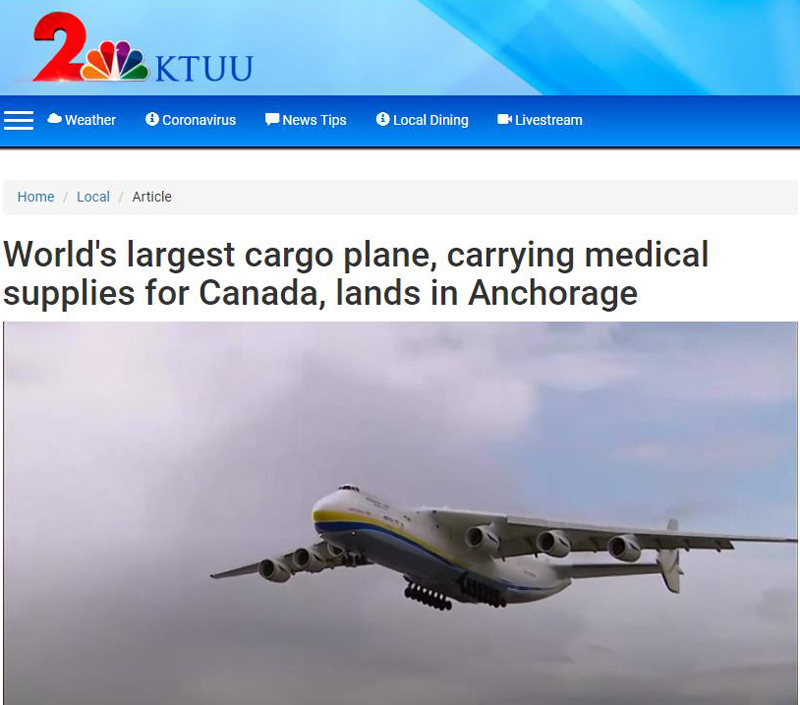
The arrival of the Antonov 225 in Anchorage was announced in advance by the media, which allowed a large crowd to stand near the airport and monitor the approach of the aircraft. The following link allows you to view the approach and arrival: KTUU Video Antonov 225
At 5:35 on the KTUU video, we can see a Fedex MD-11F. It is worth mentioning, because this was a very impressive plane at the time of its conception, but companies are progressively getting rid of it due to the age and fuel costs associated with its operation. Today, the aircraft is only used for the transport of goods. The production of aircrafts of this size, with three engines, was stopped years ago. There is a good chance that the Antonov 225 will continue to fly long after the MD-11F has made its last flight. (Edit: The Russians destroyed the Antonov 225 during the invasion of Ukraine)
After taking off from Anchorage in the morning of May 1st, the Antonov 225 arrived in Mirabel, Quebec, in the evening of the same day at around 8:22 p.m. The aircraft’s flight path (ADB3381) could be followed on Flightradar24 at the time of its approach for Mirabel (CYMX).
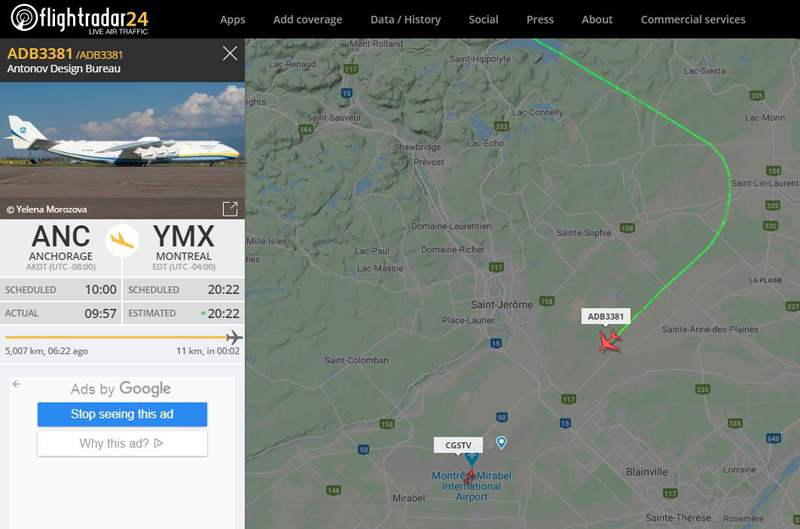
We can see on the Flightradar24 screen capture that a helicopter (C-GSTV) is positioned to film the arrival of the world’s biggest aircraft. It is an AS 350 BA from TVA, a French-language news media in Quebec.

Source : FlightAware.

Photo taken by Martin Chevalier.
YQBspotting has posted a very interesting video of the Antonov 225 arriving with its cargo of medical equipment in Mirabel, Quebec.
Andy St-André, from TVA, posted a video of the unloading of medical equipment on his Twitter account.
The photo below shows the unloading operation. The employees wore protective equipment against the coronavirus.

Photo : Joël Lemay/Agence QMI.
Several challenges were encountered for this flight to be a success: the language barrier, the verification of equipment quality (contaminated material is not of a big help), the airport operation’s requirements from China, customs limited hours of operation, maximum daily time in service for the Antonov 225 crew, international competition for slot times and orders, initiatives from some countries to acquire shipments not intended for them, etc. But finally, after hard work, Quebec finally received the precious cargo.
The last video from YQBspotting shows the Antonov 225’s departure.
Click on the link for more articles on aviation photography on my blog.
